Home »
Computer Networks
Computer Networks - II (Classifications & Architecture)
Learn: In this article, we will focus on network classification based on the use of computer nodes. This article also comprises their types, architecture, advantages and disadvantages.
Submitted by Abhishek Jain, on August 09, 2017
Computer networks that are commonly used today may be classified as follows:
- Based on geographical area: LAN, WAN, MAN, PAN etc. which were explained in previous article Computer Networks.
-
Based on how computer nodes are used:
- Client Server Networks (CSNs)
- Peer-to-Peer Networks (PPNs)
- Value-added Networks (VANs)
1) Client Server Network (CSN)
CSN basically consists of two computers, client computer and server computer. The client computers are dummy computers, which simply send requests to the server computers, whereas the server computers receive and execute the requests sent by the client computer. CSN is also known as the client server architecture. This architecture is a two-tier architecture, which is divided into two layers. The first layer comprises of the user interface that is located on the client’s desktop.On the other hand, the second layer is the database management layer, which is located on the server machine so as to provide service to the clients.
In CSN, a client computer sends a request related to processing of data to the server. The server receives the request from the client computer and processes the data.It then sends the output obtained after the processing of data to the client computer as a response to its request.
The following are the advantages of the CSN:
- There is a proper distribution of computing tasks. The task of the client computer is to send request to the server for processing of data. The server receives the request of the client computer, processes the data and sends the result back to the client computer.
- All the important data is stored on the server and only authorized persons are allowed to access the data from the server. As a result, there is greater security of data in a CSN.
- It is easy to manage the data updates as data is stored in a centralized manner on a server.
- Multiple client computers having varying hardware configuration are able to interact with a server.
The following are the disadvantages of the CSN:
- If the server crashes, the complete network breaks down.
- The load on the server increases in a CSN because there are multiple clients sending some request to a server. As a result, the network traffic increases and network congestion occurs.
Figure.1: shows a typical CSN
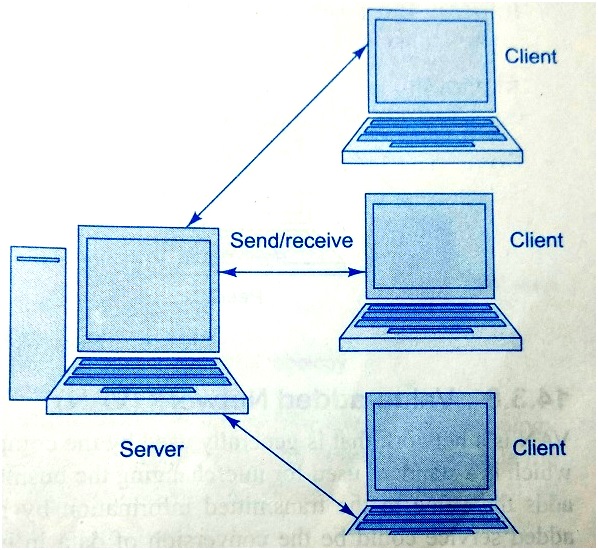
2) Peer-to-Peer Network (PPN)
In PPN, there is no separate division as clients and servers. Every computer in the PPN is treated equally and can send as well as receive the messages directly. PPN architecture cannot work under heavy load. This type of architecture is commonly used for file sharing and chatting in real time. Computers connected in this network can easily share their resources with the other components. PPN is used in a variety of fields such as business, education, telecommunications, military etc.
The advantages of PPN are as follows:
- PPN is relatively cheaper than the CSN, as the centralized server is not required.
- PPN is simpler than the CSN because computers connected in the network can communicate efficiently with each other.
The following are the disadvantages of the PPN:
- PPN is less secure because message flows freely between the computers.
- PPN is decentralized as there is no specific space for the storage of files.
- PPN is less expandable as performed and speed of network degrades when more computers are added.
Figure.2: shows the PPN
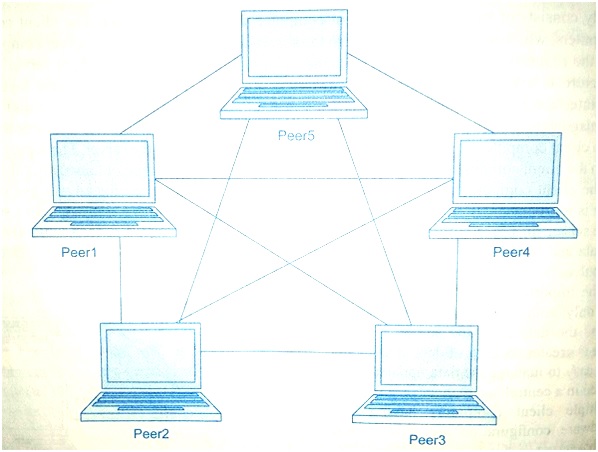
3) Value Added Network (VAN)
VAN is a network that is generally used by the companies privately for Electronic Data Interchange (EDI), which is a standard used for interchanging the business data. In other words, VAN is a network that usually adds the value to the transmitted information by providing value-added services. An example of value added service could be the conversion of data in Extensible Markup Language (XML) to EDI provided through VAN to specific companies.
Apart from providing value-added services, VAN also provides the auto error detection and correction and protocol conversion services for data modification. Error detection and correction is a technique used for detecting the errors in the transmitted data and then rectifying it. On the other hand, protocol conversion is basically used for converting a message, which has been transferred using a specific protocol to another protocol with the help of protocol converter.
Advertisement
Advertisement