Home »
Articles
Cross-Site Request Forgery (CSRF) Attacks
In this article, we are going to learn about Cross-Site Request Forgery (CSRF) Attacks.
By: Manu Jemini, on 24 JAN 2018
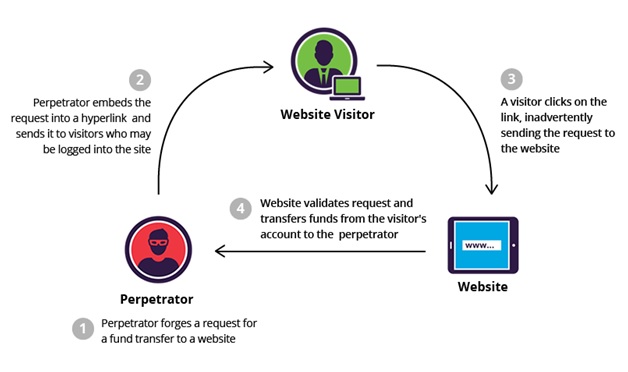
Almost every back-end developer needs to know about this attack and how to deal with it. So here’s, what is CSRF?
It is an abbreviation of Cross-Site Request Forgery, which means that an attacker can make you do some unwanted actions to exploit the user and the server itself.
The CSRF attacks are not easy to deal with. It can penetrate through all you got with POST request or saving session.
Let’s take an example, suppose your back-end server has a function to make the transaction between two bank accounts. Your function takes two account number and the amount, then just make the transaction. Now when an attacker wants to take out the money from one bank account and put it in his or her account. All he needs to do is call the function with correct parameter and make the operation. It’s easy to do.
So we what can back-end developers do to have some safety, well if you thinking about using a POST request instead of GET request to have some safety.
http://www.domainname.com?bank1=132&bank2=546&amount=1000
Now, if you are thinking you can solve it by having a session security.
Like you will check the token in the client browser and if it’s nice and sweet we will make a transaction otherwise NO.
It can be penetrated by this send a link like this to a user who has that token inside its browser. Well, it’s a social thing; we can send a link and let him do this for us. We can do this with POST method like this:
<form action="/something" method="POST" >
<input type="hidden" name="bank1" value="123" />
<input type="hidden" sname="bank2" value="987" />
<input type="submit" value="See images" />
</form>
If the user clicks he’s finished and so will the back-end developer and the bank and you are done. The Attackers will try everything possible to fill your entire browser with link like this:
< a href = "http://www.domainname.com?bank1=132&bank2=546&amount=1000"
target="_blank">See the images </a>
These kinds of things cannot be stopped by using function like this:
app.post('/something', (req,res) => {
if(security_token === session['something']){
do_the_transaction();
}else{
No();
}
})
So the question is how to protect ourselves from the treat? We will explore this in the Part – 2 of CSRF attacks (How to protect Server from CSRF Attacks?)