Home »
Articles
Best Security Practices in PHP
By IncludeHelp Last updated : August 22, 2023
Introduction
As an obliged website owner, you want to protect your visitors and keep their transactions safe. However, PHP or Hypertext Preprocessor is one vital aspect of security that gets overcooked easily. 2019's Accenture report demonstrated that security vulnerabilities have increased by 67% since 2013, including web applications that employ PHP. Hence, you must take precautionary measures to safeguard your web application's security.
An unprotected web app allows cybercriminals to rob precious details, including credit card or user data. At the same time, a data breach might significantly affect your company's future functionalities and reliability.
Moreover, SQL injection, path traversals, XSS, and local file inclusion are just a few of the assaults that PHP web applications are susceptible to. Therefore, it is necessary to dig deeper into PHP security! Well, reinforce your defense strategies with the top five Security Practices in PHP. Let us get started!
Best Security Practices in PHP
In order to build highly protected PHP applications and websites and secure your customer's confidential data, you need to start with these security practices in PHP:
1. Install a SSL certificate
An SSL certificate is crucial for transferring files safely via HTTPS instead of HTTP. This is important while amassing or transmitting sensitive details, for example, customer payment details. If your site displays login functionality, an SSL certificate can restrict you from spiteful third parties from snatching visitors' passwords and usernames. It is wise to buy SSL certificate in today's world that can give your customers a safe browsing experience.
2. Never upload different framework files to your server
When all framework files are uploaded to a web-based server, intruders become privy to the logic of the program, which offers them the opportunity to find vulnerabilities and exploit them.
The Model View Controller (MVC) file format is present across numerous frameworks written in PHP and may take the form shown below:
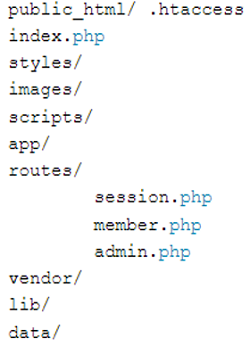
Because it is so easy to use the layout to find attack-prone files, the previously mentioned framework is simple and highly vulnerable to safety issues. When uploading to the web server, leaving out specific files is important.
3. Watch out for the XSS attacks
Cross-site scripting or XSS attack refers to the unintentional execution of remote code by a web app. It implies an XSS attack may ensue when your web app embraces user input and prints it straight to the web pages. Your web app will trigger the external code whenever an unauthorized user inserts JavaScript, HTML, or even CSS.
Go through this example below, which incorporates a form accepting user input:
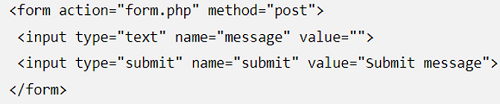
Next, it's required to print the input data straight to the web application page:
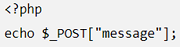
At this time, a spiteful user may include JavaScript like this. For instance, the user might add a script tag with a warning function that your web app will execute.
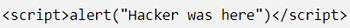
This above-mentioned tag will create a quick alert notification in the browser, and it's not detrimental. But an unauthorized user might rob the confidential user data quickly. Therefore, the best solution for impeding an XSS attack is to escape any user input to steer clear of the remote execution of code.
4. Never store password using reversible encryption
Reversible encoding is detrimental as it can quickly be decoded, making sensitive information susceptible to exposure. Next, it's harmful because this technique can sneak into your activities as the encryption & decryption strategy leaves an explicit trail of activity. Finally, it can be utilized to itemize every user's passwords, a static key for encoding and decoding.
On the contrary, you must employ a powerful hashing technique like bcrypt or Argonaut for encrypting the passwords. Hashing methods create outputs that are less susceptible to hacking than encryption methods.
This strategy makes them highly secure for passwords because minimal computing power is needed to unravel clear-text equivalents. Lastly, hashing techniques are comparatively speedier than encoding ones, making them convenient for use in apps where speed is vital.
5. Authenticate user input every time
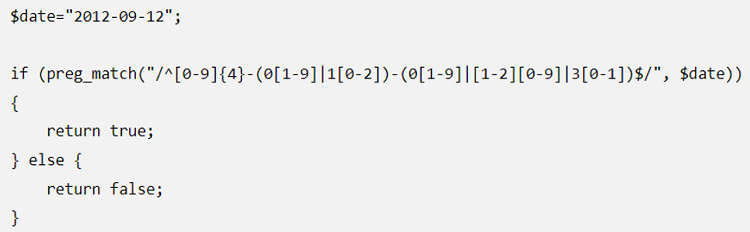
It's another significant PHP security practice. When you always authenticate user input via an input field, this ensures every piece of data possesses the right type of format and type. Usually, developers utilize regex or regular expressions to authenticate data formats, for example, contact number and date of birth. Go through the example below, which authenticates if the date of birth remains in format YYYY-MM-DD.
6. Maintain PHP code
PHP constantly improves, and every new version appears with included security patches. Therefore, it would be best to update the newest version of PHP to maximize security. Suppose you continue to use a version that is no longer supported. In that case, you risk losing support (often after three years) and losing the ability to update your software with vital safety patches and bug fixes.
It was mentioned that the PHP codes are instinctively susceptible to bugs, so there's always a scope for cybercriminals to access your web app. It suggests that your code must be as hard to break as possible. Version upgrades necessitate modifying your code, which adds tiers of security and lowers the likelihood of a hacking attempt.
Conclusion
While this list of 6 Security Practices in PHP is a great starting point if you want to boost PHP security, it's far from being global. PHP app security is a constant endeavor that needs time, continued prioritization, and buy-in within your company.
As a PHP developer, you're liable for implementing the business strategy and ensuring the establishment of full-fledged security and of the code you've created. So, prevent an attack from happening with these best PHP security practices!
Advertisement
Advertisement