Home »
Full Forms »
Technology Full Forms
What is the full form of WPA?
Full form of WPA: Here, we are going to learn about the WPA, full form of WPA, overview, types, features, advantages, disadvantages, etc.
By Anushree Goswami Last updated : March 30, 2024
WPA: Wi-Fi Protected Access
WPA is an abbreviation of Wi-Fi Protected Access. It is a security protocol or also known as encryption protocol which was created to take the place of the Wired Equivalent Privacy (WEP) or to develop upon the features of WEP for Wi-Fi networks. In 2003, it was launched with the 802.11i wireless standard. Its advanced version is WPA2 which is highly secured than WPA. From 2006, the certification of WPA2 is required for all network devices.
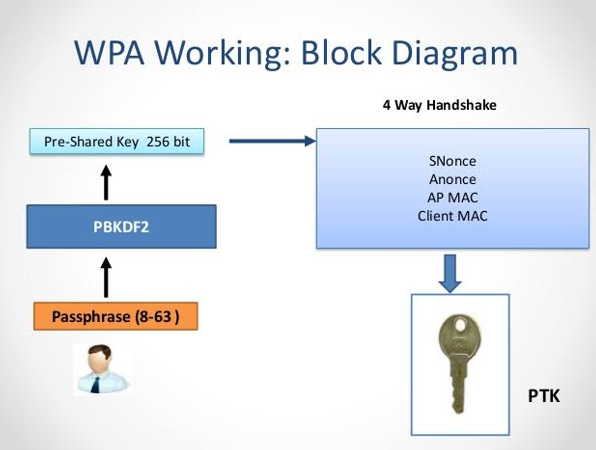
Image source: https://encrypted-tbn0.gstatic.com/images?q=tbn%3AANd9GcRZtT1EWPZxRjbeURR2GtdMrPZQH24dW9a5_7DqG5B87F5dwklk
Types of WPA
The WPA is divided into two types that provide distinct users. These two types are WPA-Personal and WPA-Enterprise,
- WPA-Personal:
This category of WPA is mainly used for small offices and personal use at home. It doesn’t need a validation or authentication server. In the case of connection of all wireless devices, a 256-bit authentication key is used.
- WPA-Enterprise:
According to the name, it is mainly used in huge corporations and large businesses. A Remote Authentication Dial-in User Service (RADIUS) authentication server is applied for automatic key generation and authentication.
Features of WPA
- It makes available for use through any of the two a level of quality technologies much effective encryption than WEP, Temporal Key Integrity Protocol (TKIP) and Advanced Encryption Standard (AES).
- The availability of built-in authentication support that is not there in WEP is offered by WPA.
- The support which is required for authentication servers or RADIUS servers is offered by WPA.
- In network security processing to make certain that data is protected, a message integrity code is integrated during the use of TKIP. The WEPs packet guarantee called cyclic redundancy check (CRC) is not that much effective in comparison to this message integrity code integration in WPA.
Advantages of WPA
In comparison between WPA and its predecessor, WPA uses much powerful and stable encryption algorithms than its predecessor. Temporary Key Integrity Protocol (TKIP) is used by WPA, through which dynamic changes occur within the key as during the transfer of data packets across the network. As there is continues change inside the key, the process of cracking the key becomes much more strenuous than that of WEP. If the need arises, WPA will automatically announce the new key.
Disadvantages of WPA
Some of the disadvantages of using WPA are, with the major issue being an incompatibility with legacy hardware and older operating systems. WPA also has a better presentation overhead and the size of the data packet increases which leads to longer transmission.
Advertisement
Advertisement