Home »
Network Security Tutorial
Network Security Architectures - Network Segmentation
By IncludeHelp Last updated : July 27, 2024
What is Network Segmentation?
Network segmentation is the practice of splitting a network into smaller subnetworks, or segments. Each segment acts as an isolated zone with its security policies and access controls. By restricting communication between segments, organizations can limit the spread of malware and unauthorized access.
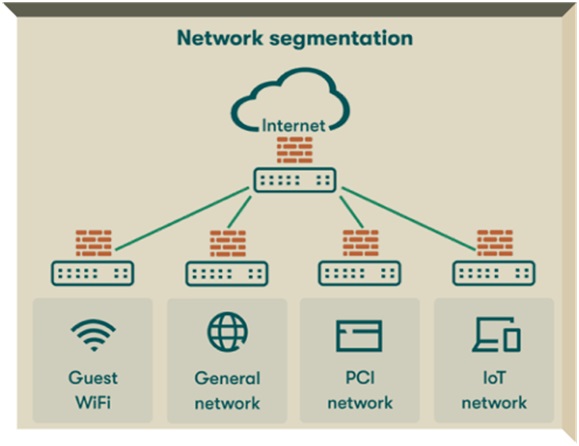
Benefits of Network Segmentation
- Enhanced Security: By isolating critical systems and sensitive data, segmentation reduces the potential damage from cyberattacks. If one segment is compromised, attackers cannot easily access other parts of the network.
- Improved Performance: Smaller network segments reduce congestion, hence improving overall network performance. Traffic can be managed more efficiently, which leads to faster data transmission and reduced latency.
- Simplified Compliance: Network segmentation helps organizations meet regulatory requirements by isolating sensitive data and systems. This makes it easier to enforce security policies and conduct audits.
- Better Management: Segmented networks are easier to manage and fix. Administrators can focus on specific segments, making maintenance and problem-solving simpler.
Examples of Network Segmentation
1. Financial Institutions
Banks and financial institutions often use network segmentation to protect sensitive customer data. For example, one segment may handle internal banking operations, while another is used for customer transactions. By isolating these functions, the institution reduces the risk of data breaches.
2. Healthcare Systems
Hospitals and healthcare providers use segmentation to protect patient data. Medical devices, patient records, and administrative systems are placed in separate segments. This ensures that a security breach in one area does not affect the entire network.
3. Retail Environments
Retailers use network segmentation to secure point-of-sale (POS) systems and customer data. A typical setup might have separate segments for sales transactions, inventory management, and customer Wi-Fi. This prevents hackers from accessing sensitive data through less secure parts of the network.
How to Implement Network Segmentation?
Use the following practices to implement network segmentation:
- Identify critical systems and data. Determine which systems and data are most important, and place them in isolated segments.
- Set security policies for each segment. Establish rules for who can access each segment, ensuring only authorized users and devices can get in.
- Use VLANs and firewalls to create segments. Implement Virtual Local Area Networks (VLANs) to create separate sections, and use firewalls to control traffic between these sections.
- Monitor network traffic and performance. Keep an eye on how data moves through the network, and make sure everything runs smoothly and securely.
- Regularly update security policies. Frequently review and improve security rules, making sure they are up-to-date with current threats.
- Perform audits to ensure segmentation is effective. Regularly check the network to ensure segments are properly isolated, and identify and fix any vulnerabilities.
Advertisement
Advertisement