Home »
Cryptography
Applications and Properties of Hash Function in Cryptography
In this tutorial, we will learn about the applications and properties of hash function in Cryptography.
By Monika Sharma Last updated : May 25, 2023
A Hash Function is a mathematical function that converts a numerical value into another compressed numeric value. The input value for the hash functions can be of arbitrary length, but the output text that it will produce will always be of fixed length.
Properties of Hash Functions
- Compressed output
- Fixed Length Output
- Pre-Image Resistance
- Second pre-Image Resistance
- Collision Resistance
Applications of Hash Functions
1) Password Storage
Due to the pre-Image resistance and collision resistance property, the hash functions are ideal to use for storing the passwords. Therefore, the values that are stored in the database are the user-Id in its original form and the hash value of the password. Therefore, whenever you enter the Id and password into a system, it searches for the user-Id, if available, it matches the hash values of the entered password and the password that is already there in the database. If both are the same, then access is granted.
This provides:
- Authentication:
Whenever the user enters the id and password, the id is matched with the one with the present in the database, and the password entered is then and there converted into its hash value and is compared with that stored in the database.
- Provides high-level security:
The hash function technique provides extreme level security, because even if the hacker or attacker is successful in breaking into the system’s database, all he gets is the user-Id and the hash value of the password, and getting the original password form this hash value is almost impossible.
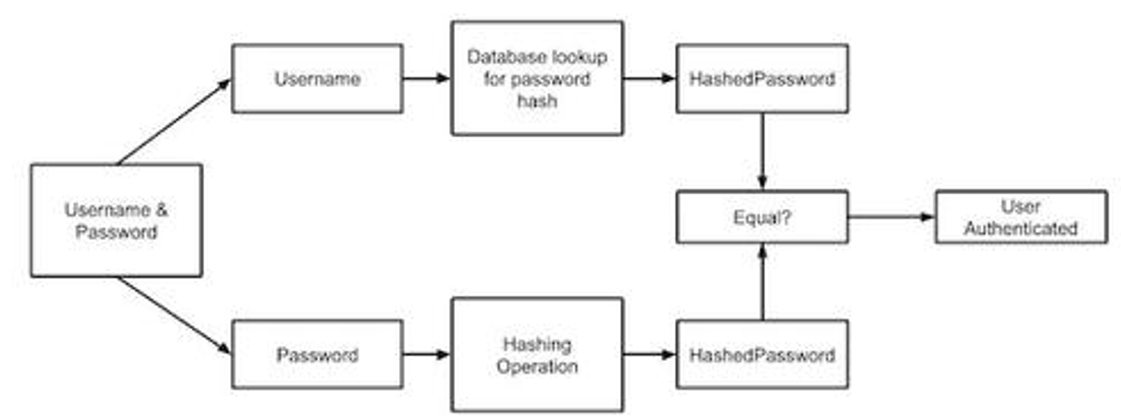
Fig. The storage and Authentication methods for Id passwords
2) Data Integrity Check
To maintain the data integrity, the sender sends both the message and its hash value to the user. The Receiver then checks whether the hash value of the message is the same as the hash value sent by the sender. This ensures that no modification has been done in the data while being transmitted. This process of integrity checks can be seen in email systems, messaging applications, etc. However, as everything takes place in the back-end, the user cannot identify this process.
3) Digital Signature
A signature is usually used to bind signatory to the message. The digital signature is thus a technique that binds a person or the entity to the digital data. This binding ensures that the person sending the data is solely responsible for being for it and this binding can be verified by the receiver and the third party. This digital signature is also stored using hash functions so that no one’s signature can be stolen and be misused.
Advertisement
Advertisement