Home »
Cryptography
Substitution Techniques and Its Types | Cryptography
Cryptography | Substitution Techniques: In this tutorial, we will learn about the substitution techniques of Cryptography, and its different types.
By Himanshu Bhatt Last updated : May 24, 2023
As we already discussed what are the Substitution techniques and one of its type Ceasar Cipher? So we are not discussing it here for that please refer to Cryptography: CeasarCipher here: Cryptography: Caesar Cipher and its Python Implementations
Types of Substitution Techniques
1) Mono-alphabetic Cipher
Predictability of Caesar Cipher was its weakness once any key replacement of a single alphabet is known then, the whole message can we decipher and almost 25 attempts are required to break it.
In this technique, we simply substitute any random key for each alphabet letter, that is 'A' can be being replaced with any letters from B to Z and 'B' can be changed to rest of the Alphabets but itself and so on. Let's say we substitute A with E that doesn't mean that B will be replaced by F.
Mathematically, we have 26 alphabet permutation which means (26 x 25 x 24 x...2) which is about 4 x 1026 possibilities.
There is only one problem with it and that is short text created using this technique, a crypto analyst can try different attacks solely based on her knowledge of the English language. English analyst found that the probability of occurrence of the letter P is 13.33% which highest followed by Z with 11.67% and occurrence of letters like C, K, L, N or R is negligible. A cryptanalyst can try various alphabets in place of cipher-text alphabet or she can look for repeated patterns of the word for is example word 'to' or 'is' occur frequently in English so she can try replacing all the T's and O's from the cipher-text and deduce further to three letter words like 'the', 'and' and so on.
2) Homophonic Substitution Cipher
The Homophonic substitution and mono-alphabetic substitution are very much alike. Like in plain cipher substation we replace an alphabet with a key but in case of Homophonic Substitution, we map an alphabet with a set of fixed keys (more than one key). For instance, A can be replaced with H, J, O, P and B will replace with any of the following inspite of A's key set D, I, W, Z etc.
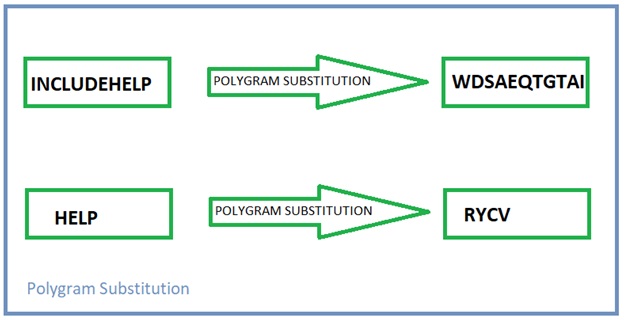
3) Polygram Substitution Cipher
In Polygram substitution cipher, instead of replacing one plain-text alphabet we simply replace a block of the word with another block of a word. Example, 'INCLUDEHELP' will change to 'WDSAEQTGTAI' whereas 'HELP' will replace to 'RYCV'. This is true that the last four letters are the same but still different in both words.
4) Polyalphabetic Substitution Cipher
Polyalphabetic Substitution cipher was introduced by Leon Battista in the year 1568, and its prominent examples are Vigenère cipher and Beaufort cipher.
We use multiple one-character keys, each key encrypts one plain-text character. This first key encrypts the first plain-text character, the second the key encrypt the second plain-text character and so on, after all, keys are used then they are recycled. If 50 one-letter keys, every 50th character in the plain text would be placed with the same key and this number (in our case, 50) is period of the cipher.
The key points of the polyalphabetic substation cipher are the following:
- It uses a set of related mono-alphabetic substitution rules.
- The ruleused for transformations determined by the key it uses.
Advertisement
Advertisement