Home »
Cryptography
Electronic Code Book (ECB) in Cryptography
Cryptography | Electronic Code Book (ECB): In this tutorial, we will learn about the electronic code book, its advantages, disadvantages, and example.
By Monika Sharma Last updated : May 25, 2023
Electronic Code Book (ECB)
This Electronic Code Book (ECB) is cryptography as a mode of operation for a block cipher, with the characters the main things that every feasible block of plaintext or an original text has a corresponding characteristic of ciphertext value and vice versa. In other words, the same or main plaintext or original value will always result or work in the same ciphertext value.
Electronic Code Book(ECB) is used when a volume or character of plaintext is separated or divided into several blocks of data, each or every of which is then encrypted independently divides it of other blocks. Otherwise, Electronic Code Book has the ability or capacity to support or promote a separate encrypted key for each block type in cryptography.
However, this Electronic Code Book is not a good system or process to use with small or little block sizes (for example, less than 40 bits in a plain text) and identical or properly encryption modes in cryptography. This is due to some particular words and phrases that may be reused again often enough or more so that the same repetitive or repeated part-blocks of ciphertext can emerge or mixed, laying the groundwork for a codebook attack where the plaintext or original text patterns are fairly obvious for this. However, security or privacy may be better if random pad bits are added to each block in cryptography.
On the other hand, 64-bit or larger or greater blocks should contain enough or more unique characteristics (entropy) to make a codebook attack unlikely to succeed in this ECB.
In the form of error correction, any bit errors or defects in a ciphertext block affect decryption of that block only of plaintext. This is the Chaining dependency is never an issue in that reordering of the ciphertext blocks will only rebook the corresponding plaintext or original text blocks, but never affect decryption in cryptography.
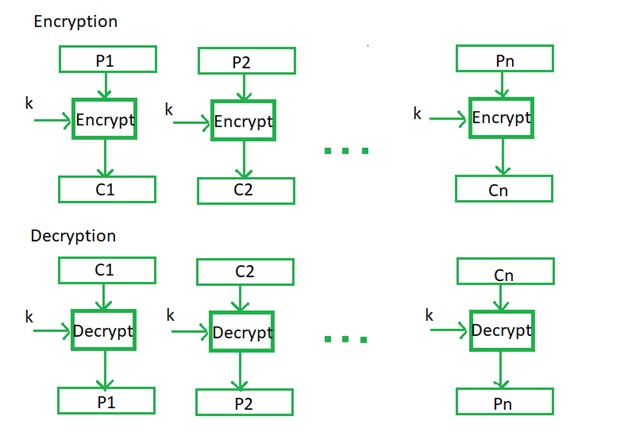
Image source: https://www.geeksforgeeks.org/block-cipher-modes-of-operation
Electronic Code Book (ECB) Advantages
- The parallel encryption of particular blocks of bits is possible or feasible, thus it is a faster way of encryption for this.
- The simple way of a block cipher is this ECB mode of operation.
Electronic Code Book (ECB) Disadvantages
- This is prone to cryptanalysis in cryptography since there is a direct or straight relationship between plaintext or original text and ciphertext.
Electronic Code Book (ECB) Example
Different from apart from using a password or message to generate an encryption key, which completes encrypted the keyspace, we have the problem of the algorithm used to process the plain text or original text. If this is ECB we have repeating cipher blocks for the same plain text or original text.
As I take "eeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee" and encrypt with as the 3-DES and a cryptography key of "bill12345" we get,
1122900B30BF1183 1122900B30BF1183 1122900B30BF11831 122900B30BF1183 1122900B30BF1183 1122900B30BF1183 7591F6A1D8B4FC8A
Here, we can see that the word "e...e" values are always coded with the same ciphertext in cryptography. As 3-DES has message blocks of 64-bits, then 8 'e' values will fill each block in the way of cryptography.
[eeeeeeee] [eeeeeeee] [eeeeeeeee]
[eeeeeeee] [eeeeeeee] [eeeeeeee]
[eeeeee PADDING]
Here, we can say that the word "eeeeeeee" maps to the cipher text of 1122900B30BF1183 as cipher text.
Electronic Code Book (ECB) Security Challenges
The ECB mode is rather simple in realization for the cryptography. It is possible or feasible to encrypt/decrypt the blocks of data or characters in parallel as there is no dependence between blocks of the plaintext or original text. In case of failure or failure of the encryption/decryption in the cryptography, the mistake extends only within one block and doesn't influence others for this.
Limitations or Restriction of ECB Encryption Scheme
- If blocks of the clear or original text are identical or similar to the corresponding blocks of the ciphertext will be identical or similar too. Otherwise if in the ciphertext some blocks are identical or similar, the corresponding or particular blocks of the clear or original text are identical or similar too. The cryptanalyst of cryptography can decipher or encrypt only one of these blocks of cryptography to find the contents of all of them.
- In another way case the blocks are independent or free itself becomes possible or feasible to replace or change some blocks of the ciphertext without knowledge of a cryptography key. The malefactor can change the part of blocks in the message with blocks intercepted during the previous message on the same cryptography key.
- In fact case of drop or insertion at least of one bit into ciphertext there will be a shift or replaced of bits and borders of blocks that will lead to wrong or incorrect decoding or decrypt of all subsequent blocks ciphertext in cryptography (it can be fixed or mixed by realization of control or work methods of borders of ciphertext blocks in the cryptography).
Advertisement
Advertisement