Home »
Cryptography
Cipher Block Chaining (CBC) in Cryptography
Cryptography | Cipher Block Chaining (CBC): In this tutorial, we will learn about cipher block chaining, its advantages, disadvantages, example, and security challenges.
By Monika Sharma Last updated : May 25, 2023
Cipher Block Chaining (CBC)
This is a Cipher block chaining (CBC) is a cryptography mode of operation for a block cipher (one in which a sequence of bits are encrypted as a single unit or a block with a ciphertext or encrypted key applied to the entire block of the cryptography). Cipher block chaining uses what is known as an initialization vector (IV) of a certain length of a character. There are one of its key characteristics is that it uses chaining the working mechanism that causes the decryption of a block of ciphertext to depend on all the preceding ciphertext blocks. As a result, the entire validity of all preceding blocks is contained in the cryptography immediately previous ciphertext block. A single-bit error of the cryptography in a ciphertext block affects the decryption of all subsequent blocks. Rearrangement of the order of the ciphertext blocks causes with this decryption to become corrupted. Basically, in cipher block chaining, each plaintext block is XORed (see XOR) with the immediately previous ciphertext block and then encrypted of the cryptography.
They are the identical ciphertext blocks can only give the result if the same plaintext or original text block is encrypted using both the same encrypted key and the initialization vector(IV), and if the ciphertext block order is not changed or rearranged. It has the advantage over the Electronic Code Book mode in that the XOR'ing process hides plaintext patterns in this way.
The initialization vector(IV) should be different for any two messages encrypted with the same cryptography key. Though the initialization vector need not be secret or placed, some applications may find this desirable and different.
Cipher block chaining or CBC is an advanced or better made on ECB since ECB compromises some security or privacy requirements. In the CBC, the previous cipher block is given as input to the next encryption algorithm after XOR with an original plaintext block of the cryptography. In a nutshell here, a cipher block is produced by encrypting an XOR output of previous cipher block and present plaintext or original text block.
The process is illustrated here,
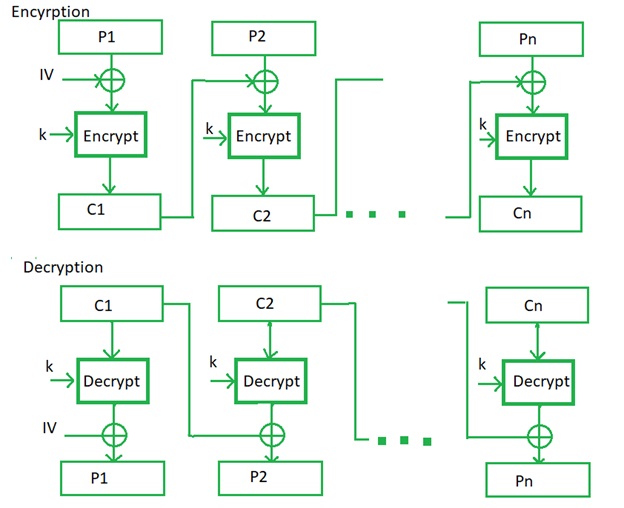
Image source: https://www.geeksforgeeks.org/block-cipher-modes-of-operation/
Cipher Block Chaining (CBC) Advantages
- This is a CBC that works well for input greater than b bits.
- CBC is the best authentication mechanism for this.
- Better resistive nature towards cryptanalysis than ECB in the process.
Cipher Block Chaining (CBC) Disadvantages
- This is the parallel encryption is not possible since every encryption requires the previous cipher of the cryptography.
Cipher Block Chaining (CBC) Example
We can let's look at applying CBC. Let's start with a message of "bred", and a key of "bert", and use and IV of 1 as which gives: "1AC9C54C951E180E0000000000000000".
Next, we'll change to an IV of 2: which gives, "D27FA68C6AC794200000000000000000"
Then, Next, we will apply it to 3DES, which uses a 112-bit key, and an IV value which is 8 bytes. Let's take an example with a message of:
The message is "The quick brown dog jumped over the lazy fox".
and a key of: 1234567890123456ABCDEFGH
If we use an IV of "12345678" we get the point:
E6B6345F1015380284481BBCFFB9052A227FC14F73072E8D5
007AC01DFEDCC2BCBCE1EB14A95ED60BA1A44700F4E18AE
but if we use this IV of "23456789" we can get the way
5BF29657E6064EB99E52ACC8E3A6808A761A86A7EE85C25C
327022C30D939D3A8A41A9CD42689AA4481FF20155816A8C
So, at least, it will change of different IV
values for the cryptography.
Cipher Block Chaining (CBC) Security Challenge
The main feature of this scheme of encryption is that identical blocks of the clear text belong to one message, are ciphered into various blocks of ciphertext.
Here are the main characteristics of this scheme are,
- If one bit of the transferred message will be corrupted or destroyed, it will damage the one more particular block. Other blocks would be safe from this damage.
- Case of loss or an insert at least one bit into ciphertext, there will be a shift of bits and borders of blocks that will lead to wrong decryption of all subsequent blocks of ciphertext of the cryptography.
- The factor can add blocks by the end of the ciphered message, supplementing with that a clear-text or original text.
Advertisement
Advertisement