Home »
Cryptography
Introduction to Cryptography
In this tutorial, we will learn Cryptography, its Introduction, security goals, cryptography attacks (types) and threads to security goals.
By Himanshu Bhatt Last updated : May 24, 2023
Cryptography Introduction
Cryptography is a method of protecting information and communications through the coding so that only those for whom the information is intended can read and process it.
In computer science, cryptography is used for securing the information and communication techniques derived from mathematical concepts and algorithms, to transform messages in ways that are hard to decipher. These algorithms are used for various cryptography techniques such as cryptographic key generation, digital signing, verification to protect data privacy, web browsing on the internet, and confidential communications such as credit card transactions and email.
Security Goals
Let's discuss the three security goals...
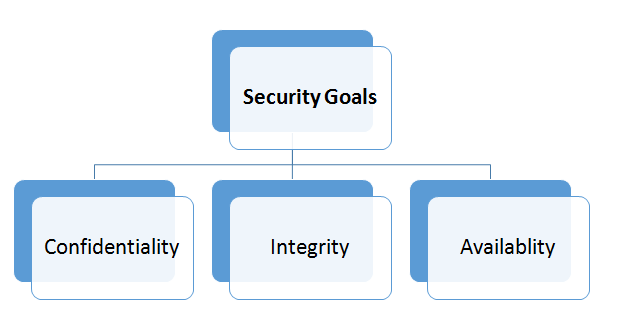
1) Confidentiality:
Confidentiality is probably the most common aspect of information security, we need to protect it. An organization/company needs to protect against that malicious action that endangers the confidentiality of its information. In the military, concealment of sensitive information is a major concern. While in Industry, hiding some information from the competitors is crucial.
2) Integrity:
Information changes constantly. Like in banks, when a customer withdraws or deposits money, the balance of his account needs to be changed.
Integrity means that the change needs to be done only by authorized entities and through the authorized mechanism. Not only malware acts but an interruption in the system can also create unwanted changes in some information can also violate the integrity of the system.
3) Availability
An organization may have a lot of information which need to be available for access to the authorized entities. Information is useless if it is not available. The unavailability of information is as harmful for an organization as the lack of confidentiality or the integrity.
Now we will head towards the type of Cryptographic Attacks...
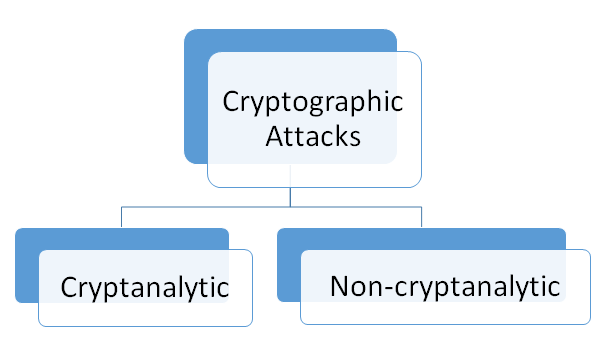
Cryptanalytic Attacks
These attacks are a combination of statistical and algebraic techniques aimed at ascertaining the secret key of a cipher. These methods inspect the mathematical properties of the cryptographic algorithms from uniform distributions. All the cryptographic algorithms act upon the message distribution and convert it using the key to a ciphertext distribution which looks random. The objective of cryptanalysis is to find properties of the cipher which does not exist in random function. The attacker thus guesses the key and looks for the distinguishing property. If the property is detected, the guess is correct otherwise next guess is tried. Efficient attacks will adopt a “Divide and conquer” technique to reduce the complexity of the guessing key from the brute force search complexity. An attack is said to be successful if the guessing complexity is lesser than the brute force complexity.
Non-Cryptanalytic Attacks
These are the attacks which do not exploits the mathematical weakness of the cryptographic algorithm. However, the three goals of security, namely confidentiality, integrity, and availability are still threatened.
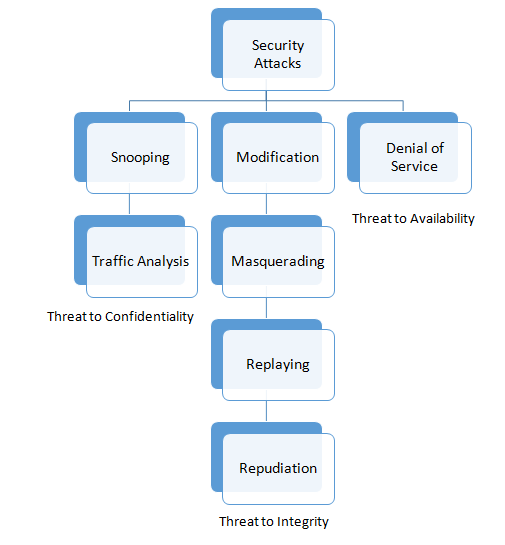
Attacks to Confidentiality
- Snooping: It refers to unauthorized access to or interception of data. For example, a file transferred through the internet may contain confidential information and an unauthorized entity may intercept the transmission and use the content for his own benefit.
- Traffic Analysis: Though encipherment of the data may make it nonintelligible for the interceptor, he can obtain some other type of information by monitoring online traffic. For example, she can collect the electronic addresses like Email address of the sender or the receiver.
Attacks Threatening Integrity
- Modification: If an attacker modifies the information to make it beneficial to himself by intercepting or accessing information. Example, a customer sends a message to a bank to do some transactions but the attacker intercepts the message and changes the type of transaction to himself, also he can delete, delay or harm the system.
- Masquerading: When an attacker tries to impersonate somebody else that is called masquerading. Example, an attacker might steal bank card and PIN of a bank of a customer and pretend to be that customer.
- Replaying: The attacker obtains a copy of a message sent by the user and later tries to replay it. Example, a person sends a request to her bank to ask for payment to the attacker, who has done a job for her. The attacker can receive another payment from the bank by intercepting the message and again send it to the bank.
- Repudiation: This attack is different from the other because it performed by one of the two parties in the communication: the sender or the receiver. The sender of the message might later deny that he sent the message; the receiver of the message might later deny that he has received the message.
Attacks Threatening Availability
Denial of Service: Denial of Service (DoS) is a very common attack. It may slow down or totally interrupt the service of a system. It can be done in several ways as an attacker might send so many bogus requests to a server’s response to a client, making the client to believe that the service is not responding. An attacker may also intercept and delete a server’s response to the client or intercepting requests from the client, causing the client to send request many times and overload the system.
Cryptography
Cryptography derived from Greek origins means "secret writing". However, we use the term to refer to transforming the message to make them secure and immune to attacks.
Earlier, cryptography referred only to decryption and encryption of message using the secret keys, but today it is different and involving three distinctive mechanisms, these are:
Symmetric-Key Encipherment
In Symmetric-key Encipherment(secret-key cryptography), an entity, saysMeera, can send a message to another entity, say, Ram, over an insecure channel with the assumption that someone, says Kiran, cannot understand the contents of the message by simply eavesdropping over the channel.
Meera encrypts the message using an encryption algorithm; Ram decrypts the message using the decryption algorithm. Symmetric-key encipherment uses a single secret key for both encryption and decryption. Encryption/decryption can think of as electronic locking. In symmetric-key enciphering, Meera puts the message in a box and locks the box using the shared secret key; Ram unlocks the box with the same key and takes out the message.
Asymmetric-Key Encipherment
In Asymmetric-Key encipherment (public key cryptography), we have the same situation as symmetric-key encipherment but now there are two keys instead of one: one public key and another one private key. To send a secured message to Ram, Meera first encrypts the message using Ram’s public key. To decrypt the message, Ram uses his own private key.
Hashing: In Hashing, a fixed-length digest is created out of the variable-length message. The digest is normally much smaller than the message. To be useful, both message and digest must be sent to the Ram. Hashing is used to provide check values, which were discussed earlier in relation to providing data integrity.
References
Advertisement
Advertisement